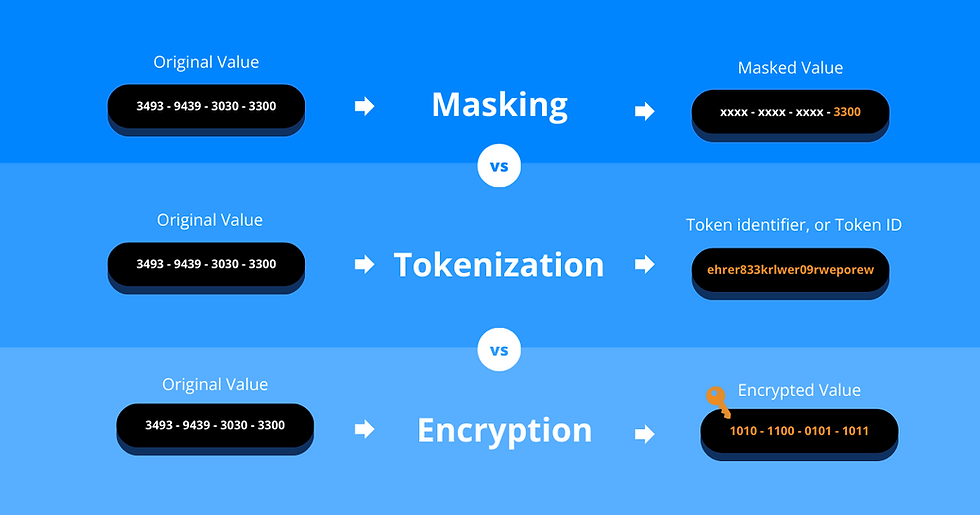
3 Signs You've Outgrown Your Tokenization
- Jun 6, 2025
- 3 min read
Updated: Jun 16, 2025

Data tokenisation has long been a trusted method for protecting sensitive data, particularly for organisations that handle large volumes of personal and regulated data. But as technology advances, regulatory demands tighten, and business needs grow more complex, what once worked well can now lead to bottlenecks and unnecessary risk.
If your tokenization strategy feels cumbersome or limiting, you're not alone. Here are three clear signs it's time to rethink your approach—and how a modern, integrated solution can transform your data security and usability.
1. Your Teams are constantly asking for detokenized data
When tokenisation was first introduced, it often served a narrow purpose—shielding data while at rest or in transit. But today's data-driven organizations require much more: analytics, reporting, AI training, and operational workflows that depend on meaningful data access.
If your analysts and data scientists frequently request detokenized versions or create parallel data flows to complete their work, instead of being able to work directly with protected data, it's clearly a red flag. This workaround not only increases the risk of exposure but also requires additional manual effort and yields inconsistent outputs.
Advanced tokenisation techniques, such as format-preserving encryption, allow data teams to query and analyse data directly within platforms such as Apache Spark, Hive, and Impala, without ever exposing raw sensitive information. Format-preserving encryption is a method that protects sensitive data by encrypting it in a way that maintains the original format, length and character set of the input. By enabling secure access to meaningful but still protected values, organisations can make better use of their data without compromising on privacy or compliance.
2. PII data is moving between systems for tokenization
Some legacy tokenisation solutions depend on dedicated hardware, external APIs or separate vault-based processing environments. This often means that sensitive data must be extracted from your core platform, transferred for tokenisation, and then returned before it can be used—sometimes more than once.
These additional steps increase the cost, latency and complexity of data workflows. They can also create points of vulnerability, especially when data needs to move between on-premises and cloud environments.
A more efficient approach is to run tokenisation where your data already lives. In a modern data platform such as Cloudera, tokenisation can be embedded directly into your data pipelines using native services and user defined functions. This helps simplify architecture, reduce processing time, and ensure protection is always applied as part of your standard workflows.
3. Compliance depends on manual processes
As regulations become more detailed and audits more frequent, many organisations are discovering that their approach to governance and access control is hard to maintain.
In particular, if your compliance workflows rely on spreadsheets, scripts, or siloed tools, it becomes difficult to maintain control, and the risk of error or oversight increases. These methods may have worked when systems were simpler, but they struggle to keep pace with the volume and speed of modern data across hybrid cloud environments.
Effective tokenization integrates tightly with your governance stack. For example, Cloudera’s ecosystem supports policy enforcement via Apache Ranger, encryption key management through KMS, and audit logging with Atlas. When tokenization is part of this unified framework, compliance becomes automated, transparent, and scalable, freeing your security teams to focus on risk reduction rather than firefighting.
It's Time for a Tokenization Upgrade
If any of these signs resonate with your organization, it’s time to revisit your tokenization strategy. Legacy approaches are no longer sufficient for today’s data challenges. Fortunately, many of the issues stemming from legacy tokenization can now be resolved with newer, more straightforward solutions that seamlessly integrate with your data platform, delivering a brighter future for your data security and usability.
SecureToken by Bluemetrix is purpose-built for the Cloudera. It supports native, vaultless tokenisation that scales with your data, supports compliance, and lets teams continue working securely with protected data.
To explore SecureToken and evaluate its fit for your organisation, you can start a free 30-day trial at www.bluemetrix.com/securetoken